Security
IFS Applications security has been designed with modularity and flexibility
in mind. This allows enterprises to select the level of security that is right
for them, balancing threat prevention with simplicity and ease of use.
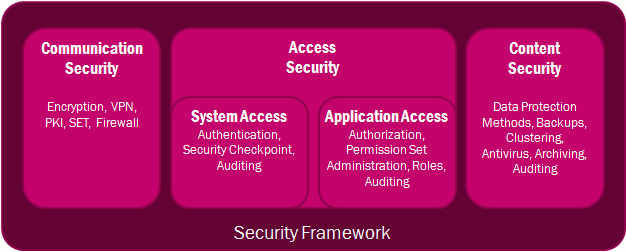
Communication Security
- IFS Application extrenal network communication is always protected by
TLS/SSL encryption (HTTPS). Since IFS Applications is based on standard
technologies it can be used
with standard network-level security solutions such as firewalls, proxies and VPN-networks.
If exposing the IFS Webserver/Middlewareserver to internet, URL filtering in proxy can be used to limit which URL's should be available publicly. Demilitarized zone (DMZ), hardened perimeter defense, and other firewall
strategies; all of these can be used with IFS Applications.
Access Security
- System Access - All client requests to IFS Applications will require
authentication. User credential validation is performed through the OpenID
Connect-protocol.
- Application Access - The IFS Applications architecture enforces a uniform role-based
security model across the entire application. The role-based authorization model of IFS Applications ensures that only
authorized employees have access. Authorization can be performed by function
(what can I do?) and data (what ranges of data may I see?).
Content Security
- IFS Applications relies on standard network, operating system, and
database security, and does not add or require a proprietary layer. Only
established technologies with known security properties are used, including
OpenID Connect, HTTP and SSL/TLS.
- IFS Applications has a built-in log function that tracks all modifications
to data, including details of what was modified by whom and what the previous
values were. This creates a clear audit trail of all changes or removals of
data.
Contents

