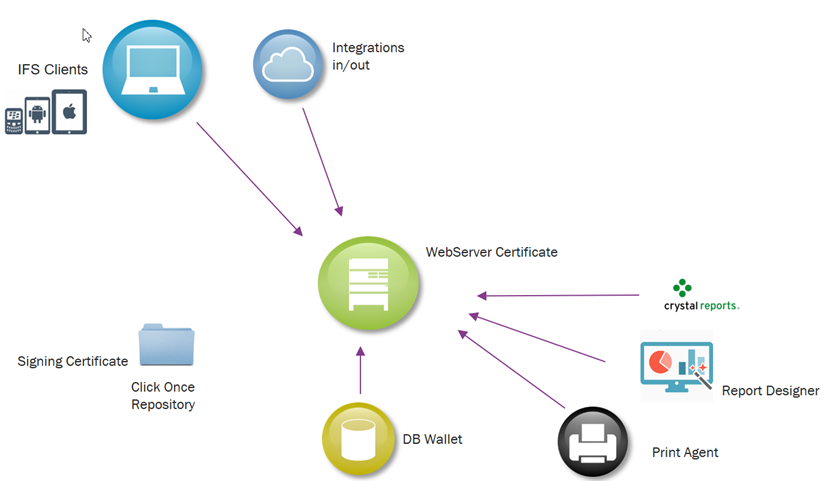
IFS Applications requires secured communication (HTTPS) for all installation types. This implies that all clients that connects to the IFS Middleware Server have to have or obtain trust to the certificate used by the Middleware Server. The certificate to trust might be issued to either the mws webserver itself or an external proxy.

When connecting to any server that require secure communication the client must trust the keys that the server offers to encrypt the traffic. The client must trust that the key is actually coming from the server the client thinks its connection to. Together with the encryption keys (Public keys) the server sends a signed Certificate that refers to the CA that signed the Servers Certificate. IF the client trust that specific CA then the client will also trust that the keys comes from a trustworthy server and use the keys. The client knows when to trust a specific CA if the CA is in the clients truststore.
On a windows client this list of trusted CA's can be seen using the application "certmgr" from a cmd prompt.
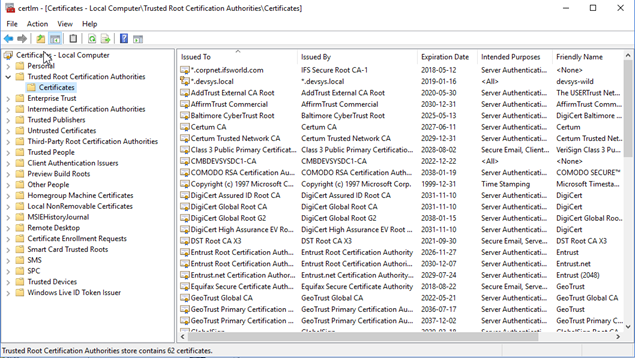
Right-Mouse-Click on "Certificates" will allow new certificates to be
imported in certmgr.
Normally it is possible to use the Internet browser for to fetch a client certificate and manually approve the validity of the certificate. This is done by pointing out the web url and accepting the certificate in the browser. Most of browsers offer possibility for exporting the downloaded certificates.
The IFS MWS client certificate (CA trust) can be found in the ifs_home in path <instance>/security/certs/import/<instance>.cer. This file can be copied to a client that needs to connect to the MWS and be imported it to a truststore.
If you need to import certificates from third party web services they need to be fetched first. It is possible to use the Internet browser for this purpose by pointing out the third-party web service and accepting the certificate in the browser. Most of browsers offer possibility for exporting the downloaded certificates.
But it is also possible to use command line tools for fetching the
certificate: openssl
and sed. Both
those tools are typically preinstalled on Linux but must be downloaded and
installed on Windows.
The command looks as follows:
Linux:
openssl s_client -connect <hostname>:<port> < /dev/null | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' > <certificate.crt>
Windows:
openssl s_client -connect <hostname>:<port> < NUL | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' > <certificate.crt>
The certificate used by Middleware Server (regardless of if importing a third-party certificate or creating a self-signed certificate) is exported to <ifs_home>/instance/<instance>/security/certs/import folder and is named <instance>.cer. IFS Installer automatically imports all certificates located in <ifs_home>/instance/<instance>/security/certs/import during one of the installer phases to its own truststore. It imports custom certificates into this truststore and merge it with the standard java truststore (cacerts). Truststores created by the installer are protected with the IFS Middleware Server administration user password. The installer will maintain the contents of the mws trusts even when a new version java is deployed in a patch/delivery.
If the certificate is not trusted by default, any standalone service that use Java (may it be a Java located in the <ifs_home> or elsewhere) must import this certificate into its trust store or any communication with the server will fail. Some 3pp integrations may require the certificate (<ifs_home>/instance/<instance>/security/certs/import/<instance>.cer) to be imported.
When the installer imports or creates a self-signed certificate it will create a structure under <instance>/security with all certificates and truststores used by the middleware server.
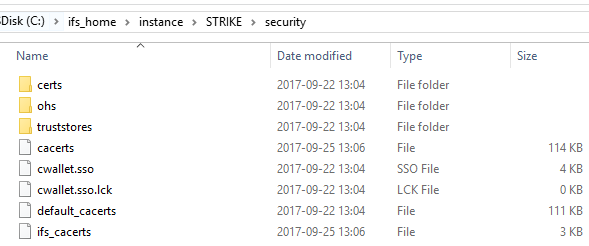
Client Certificates for OHS
certs/import/<instance>.cer
MWS Certificates (root and server)
certs/mwsCA.cer, ifs_mws.cer
OHS keystore in oracle kestore format
(orakpi)
ohs/cwallet.sso
MWS keystore
truststore/ifs_mws.jks
Java keystore
cacert is a merge of default_cacerts+ifs_cacerts. Cacert is copied to mws
java_home
DB Wallet
plsqlap_environment_tab holds a path on DB server containing a copy of the OHS
Keystore
Client Signing Certificate (.pfx)
placed anywhere but in the runtime folder.
This section is not required to be used in the IFS system, where this is
automatically handled by the installer for all certs located in
<ifs_home>/instance/<instance>/security/certs/import.
But
some 3pp integrations may require the certificate and this instruct how to
include the
<ifs_home>/instance/<instance>/security/certs/import/<instance>.cer
inte a 3pp java truststore.
A certificate is imported to a truststore by executing the following command:
<java_home>/bin/keytool -import -alias <certificate-alias> -file <certificate.cer> -keystore <truststore> -storepass <thePassword>
-alias: A descriptive name of the imported certificate. Can be chosen freely.
-file: The certificate file to import.
-keystore: The keystore or truststore the certificate shall be imported to. If you plan on using a custom truststore, specify the location and name of that here
(see below for more information) otherwise specify cacerts (<java_home>/jre/lib/security/cacerts)
-storepass: The password for the specified truststore. The default password for cacerts is 'changeit'.
Creating a new java truststore can be a convenient way of keeping track of all the certificates used for an installation. It makes it easier to get all certificates imported to a new Java installation and can be easier to maintain when certificates get old or are no longer needed.
To create a new truststore, execute the following command:
<java_home>/bin/keytool -import -alias <certificate-alias> -file <certificate.cer> -keystore <truststore>
-alias: A descriptive name of the imported certificate. Can be choosen freely.
-file: The certificate file to import.
-keystore: Specify the location for the new truststore. I.e. location and name.
It will prompt for a new password. Carefully choose a secure password for the truststore that has at least six characters.
If merging to cacerts, it's recommended to store the original cacerts together with the custom truststore. This allows you to maintain only the custom truststore and simply overwrite cacerts after merging them.
To merge an existing truststore to cacerts, execute the following command:
<java_home>/bin/keytool.exe -importkeystore -srckeystore <source_truststore> -destkeystore <destination_truststore>
-srckeystore: The trustore to be merged from
-destkeystore: The truststore to be merged to (e.g. <java_home>/jre/lib/security/cacerts).
It will prompt for the password for the source truststore and the password for the destination truststore.