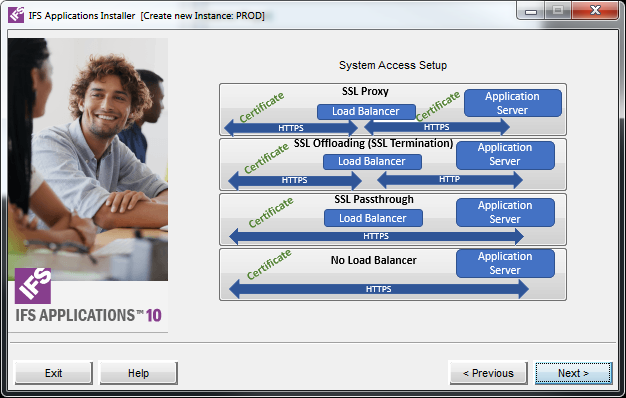
Depending on the configuration, IFS Middleware Server can use an external load balancer in front of the HTTP Server(s) to handle requests from clients. Secured communication is enforced for all installations but can be terminated at an external load balancer. In this context load balancer and Proxy are equivalent. A Proxy can be seen as the simplest form of a load balancer with only one node to distribute load to.
More information about how load balancing works can be found here.
More information about configuring HTTPS can be found under topic security.
If setting up an environment what should be accessable from public internet over a reverse proxy - please read this first.
It is possible to verify the third-party certificate password and the complete chain of trust by using the 'Verify' button.It does not test self-signed certificates: But the �Verify� button should be dimmed anyway when selecting �self-signed�.
The PL/SQL Accsess Provider in the database always communicates with the Load balancer. i.e. the database needs access to the network where the load balancer is exposed.

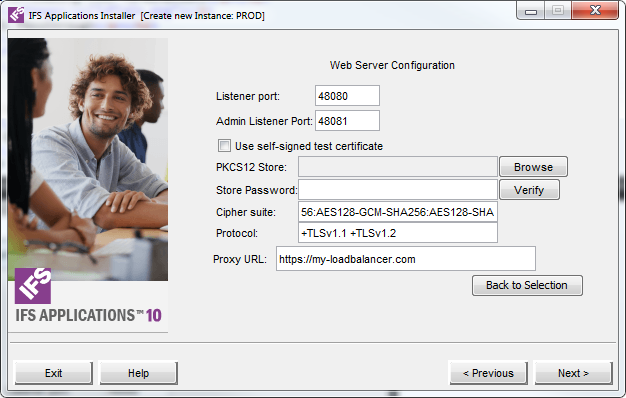
Parameter Description Listener port The HTTP Server listener port. This is the client entry point. Admin Listener Port The port for IFS Administration Applications (e.g IFS Admin Console). Import Third Party Certificate Third-party certificates are those created from certificate requests. These third-party certificates contains more than just the user certificate; they also contain the private key for that certificate. Furthermore, they include the chain of trusted certificates validating that the certificate was created by a trustworthy entity. Take the actions indicated in the exporting product to include the private key in the export, and specify the new password to protect the exported certificate.
The password must contain at least six characters. Also include all associated trust points.
Several publicly trusted certificates are automatically installed, since they are so widely used and need not be included explicitly. Under PKCS #12, browsers do not necessarily export trusted certificates, other than the signer's own certificate. You may need to add additional certificates to authenticate to your peers. Specify the location of the resulting file, containing the certificate, the private key, and the trust points together with the password.Self Signed Certificate The installer creates a certificate. Self-signed certificates can be created for convenience and is mainly for testing purposes. If you select to use a self-signed certificate you will be prompted to fill out information used to generated the certificate. Cipher Suite The cipher suite that the application server is going to use. Protocol The allowed/disallowed protocols to be used. Proxy URL The URL to the external load balancer. Protocol must start with https, port can be omitted when using the standard HTTPS port.
When pressing 'Next' the proxy certificate will be prompted for.
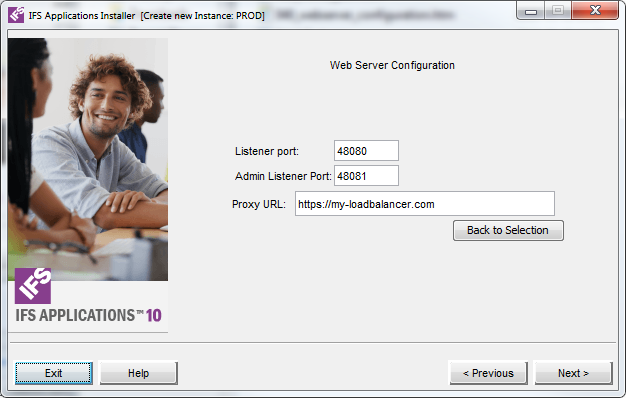
Parameter Description Listener port The HTTP Server listener port. This is the client entry point. Admin Listener Port The port for IFS Administration Applications (e.g IFS Admin Console). Proxy URL The URL to the external load balancer. Protocol must start with https, port can be omitted when using the standard HTTPS port.
When pressing 'Next' the proxy certificate will be prompted for.
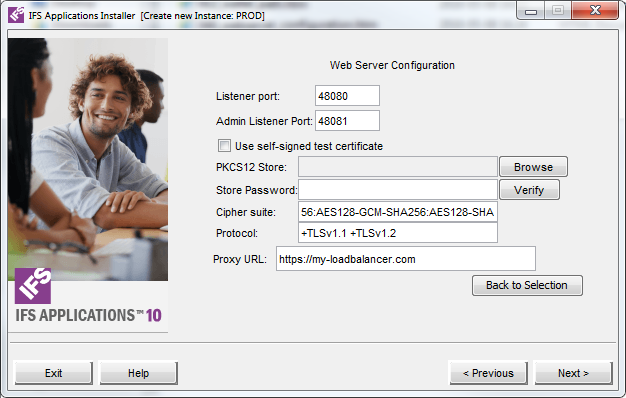
Parameter Description Listener port The HTTP Server listener port. This is the client entry point. Admin Listener Port The port for IFS Administration Applications (e.g IFS Admin Console). Import Third Party Certificate See above for more information. Self Signed Certificate See above for more information. Cipher Suite The cipher suite that the application server is going to use. Protocol The allowed/disallowed protocols to be used. Proxy URL The URL to the external load balancer. Protocol must start with https, port can be omitted when using the standard HTTPS port.
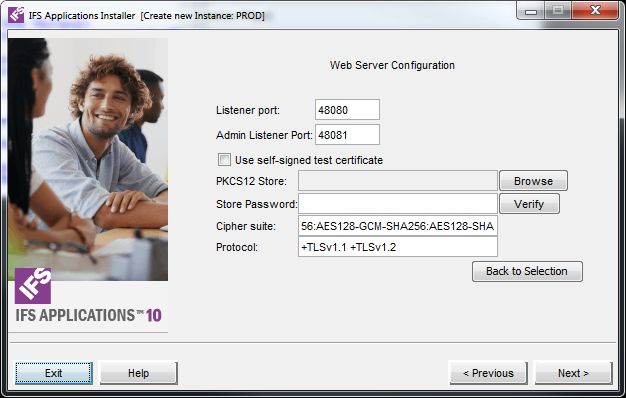
Parameter Description Listener port The HTTP Server listener port. This is the client entry point. Admin Listener Port The port for IFS Administration Applications (e.g IFS Admin Console). Import Third Party Certificate See above for more information. Self Signed Certificate See above for more information. Cipher Suite The cipher suite that the application server is going to use. Protocol The allowed/disallowed protocols to be used.
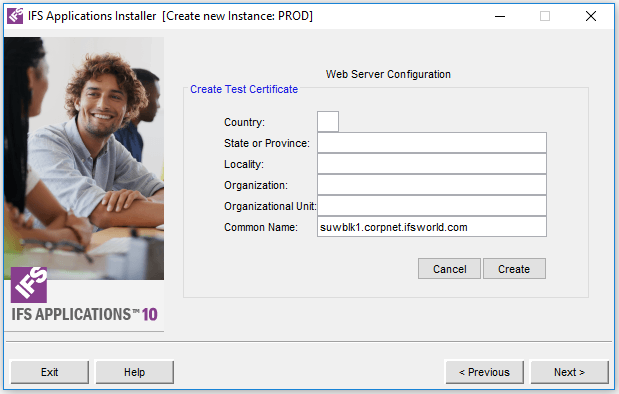
Create Self Signed Certificate form. Click cancel to exit certificate creation.
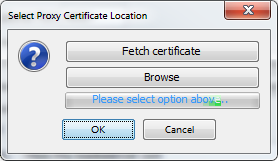
Fetch or import the certificate used by the external load balancer.
The certificate used by the load balancer is needed. It is possible to fetch the certificate but it requires the load balancer to be configured and running with a valid certificate. If that isn't possible, the certificate used by the load balancer can be imported manually.
NOTE: Installer doesn't allow store passwords with special characters.
NOTE: SSL 2.0, SSL 3.0 and TLSv1 are considered insecure and should, as the default configuration suggest, be disallowed!. Since the installer runs on Java 8, OpenSSL 3.0 and above are not supported with Java versions below 8u301 or 11.0.1 due to incompatibility with the encryption methods used in SSL 3.0.
 |
N/A |
 |
N/A |