
The role synchronization concept is simple - by adding users to a group in the Active Directory the sync job will grant a permission to the group members, while removing users will revoke the configured permission set.
Each configuration can have one or more role mappings. A role mapping is basically a mapping from a specified group in the Active Directory, to a permission set in IFS Applications. The mapping can also have an IFS User Group attribute attached to it.

The role mapping part of the configuration form.
Use the context menu in the role mapping table to bring up the dialog to add a new mapping entry. The dialog lets you enter
Note: Only the Active Directory group is required to constitute a valid mapping. Such an 'empty' mapping will however only synchronize user information and won't contain any role information. Also note that a permission set can be used in several mappings, but an Active Directory group can be mapped only once.
If you would like to edit or delete a mapping you'll have to consider a side effect. Just removing the row from the mapping table will result in leaving the group members still being granted the configured permission set. Same goes for editing a mapping entry as the old permission set will stay granted for the members. By using the IFS User Group specified for the mapping you can manually revoke the permission set for all members in the group.
The sync job does not require any specific hierarchy or naming scheme in the Active Directory. You can organize the groups in the Active Directory according to existing naming standards. However, there are a few considerations.
As an Active Directory group only can be mapped once per configuration your permission sets must be 'stand-alone'. This means that a permission set that is mapped must completely cover the role that the Active Directory group is mapped to. This can be achieved by building an hierarchy of permission sets extending each other.
The groups in the Active Directory can be organized in either a flat or a nested hierarchy. Each group in the Active Directory has a one-to-one relationship with a permission set in IFS Applications. The difference is in how the Active Directory is organized.
The sync job traverses the mapped groups in the Active Directory from top to bottom to find any descendent group. You can, if you would like to, take advantage of this and build an hierarchy of groups extending each other role wise.
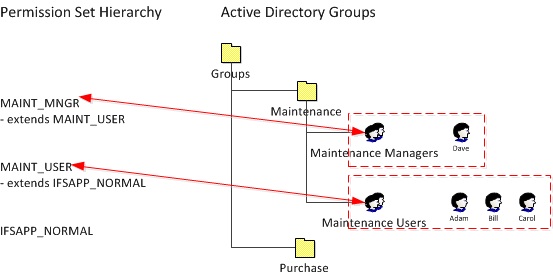 Example of flat hierarchy of groups in the Active Directory. All users in the group 'Maintenance Managers' in the Active Directory will be granted the permission set MAINT_MNGR. Users in the group 'Maintenance Users' will be granted the permission set MAINT_USER. |
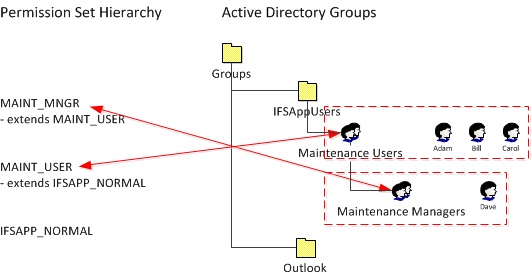 Example of nested hierarchy of groups in the Active Directory. All users in the group 'Maintenance Users', or any of its descendant members, in the Active Directory, will be granted the permission set MAINT_USER. The users in the group 'Maintenance Managers' will be granted the permission set MAINT_MNGR. User Dave will thus be granted both permission set MAINT_USER and MAINT_MNGR. |