Access Security¶
IFS Cloud security has been designed with modularity and flexibility in mind. This allows enterprises to select the level of security that is right for them, balancing threat prevention with simplicity and ease of use.
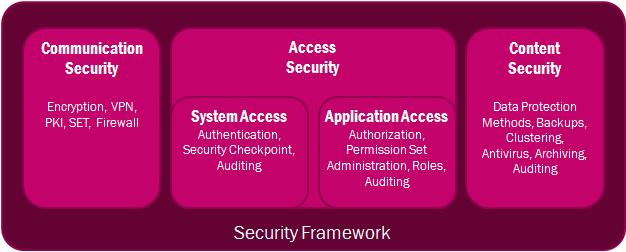
Access Security
- System Access - All client requests to IFS Cloud will require authentication. User credential validation is performed through the OpenID Connect-protocol.
- Application Access - The IFS Cloud architecture enforces a uniform role-based security model across the entire application. The role-based authorization model of IFS Cloud ensures that only authorized employees have access. Authorization can be performed by function (what can I do?) and data (what ranges of data may I see?).