Security Considerations Mobile Apps¶
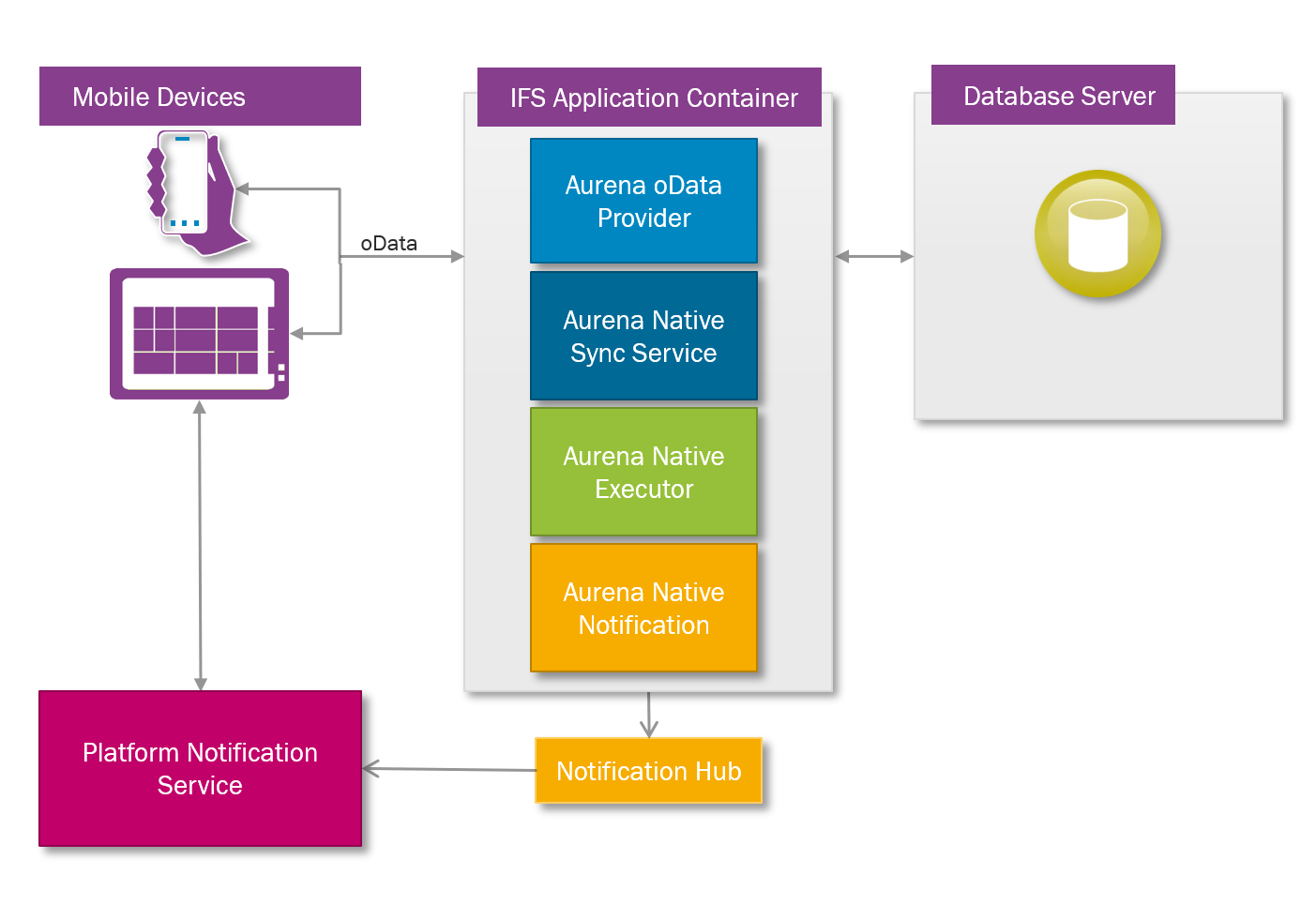
IFS Cloud Mobile works by connecting device specific applications through to the customers IFS Cloud system and communicate with IFS Cloud using oData through IFS Cloud OData Provider. IFS Cloud Mobile Sync Server prepares the data that is synchronized to the device. Both IFS Cloud oData Provider and IFS Cloud Mobile Sync Service communicates with IFS Cloud Mobile Notification, which handles the push communication to the device and IFS Cloud Mobile Executor, which handles the mobile app offline transactions.
Business logic that is specific to the mobile app runs as a projection in IFS Cloud.
Securing the device¶
Mobile apps are most often single-user apps that rely on device security to protect data. Once a device has been unlocked users can view and act on information in the mobile app. There are exceptions to this rule; multi-user apps and apps that handle sensitive data. For these apps a password must be entered every time the app is started, but once the app is up and running it can still be accessed by anyone if the device is left unprotected.
IFS recommend that our customers adhere to best practice routines for protecting their devices. This includes but is not limited to the precautions listed below:
- The level of protection required depends on the sensitivity of the data in the particular mobile app installed on the device, but a minimum protection level would include a lock screen with pass code, pattern, finger print or equivalent lock method.
- Running any app on a rooted/jailbroken device is strongly discouraged for security reasons.
- For stronger device protection IFS recommend the use of MDM (Mobile Device Management) software.
Application Distribution¶
Mobile apps are distributed through the standard channels for the different platforms; Apple App Store, Google Play and Windows Store.
User Authentication¶
Mobile app uses the same authentication mechanism as other IFS Cloud clients such as IFS Cloud Web. If IFS Cloud has been configured to use an external Open ID Connect Provider then that is what mobile app will use. For example if the system has been configured to use Azure AD then that is what mobile app will use. If multi factor authentication is required for mobile app then IFS Cloud have to be configured to use an external Open ID Connect Provider which supports multi factor authentication.
It is important to note that mobile appa always uses the DEFAULT application type when authenticating the mobile apps users. Please refer here for more information on Application Types
User Authorization¶
Protection of information in the IFS Cloud database rests on the same principles as if the mobile app were not there. This implies that what end users can do from IFS Cloud Web they can also do from a mobile app, if enabled for the system, and what they cannot do from IFS Cloud Web they cannot do from an mobile app even if the app is enabled for the system.
For mobile app dealing with sensitive data it is possible to make use of additional, app specific grants allowing customers to restrict usage of the mobile app to selected personnel. This is in addition to the regular privileges required to access the functionality through IFS Cloud Web.