Signature Service - Middletier¶
This guide is intended for Administrators of the signature service
Contents¶
- Enable IAM Clients
- Register Certificates
- Signature Extension
- Timestamp Authorities
- Digital Signature and Non Repudiation set
- Permission Sets
- Signature Extension
- Storage
- Signed Documents
- System Parameters
Enable IAM Clients¶
First of all, enable IFS_dss and IFS_dss_native IAM clients for Signature Service authentication requirements.
Register Certificates¶
Before documents can be signed all certificates required to build up a complete chain of trust needs to be imported to the signature service. IFS Signature Service trusts everything in the cacerts file distributed with Java. Root and intermediate certificates signed by a private CA or a CA that isn't included in Java cacerts must be imported. The public certificate must be registered and mapped to the correct user before it can be used to sign documents.
Certificates are validated while saving them for the first time. A background job will be validating the certificates every midnight and administrator can also validate certificates on demand. The status displayed will indicate the validation result of the certificate.
Certificate Status¶
| Status | Description |
|---|---|
| Valid | Certificate validated successfully |
| Expired | Certificate is expired |
| Expiring Soon | Certificate expiring soon |
| Revoked | Certificate is revoked |
| Not Yet Valid | Certificate can be used in future |
| OnHold | Certificate is revoked temporarily |
Certificate Requirements¶
IFS Signature Service supports RSA and ECDSA encryption algorithms. For RSA the key length should be at least 2048 bits while for ECDSA only 256 bit and 384 bit key lengths are supported. ECDSA is the recommended algorithm.
| Algorithm | Key Size | Recommended | Supported |
|---|---|---|---|
| ECDSA | 384 | ✓ | Yes |
| ECDSA | 246 | ✓ | Yes |
| RSA | 4095 | Yes | |
| RSA | 2048 | Yes | |
| RSA | 1024 | No |
Register Root and Intermediate Certificates¶
Root certificates and, if needed, intermediate certificates are imported from solution manager. All certificates are validated during the import to make sure it can be used properly. If the certificate is not valid it will not be imported. If the certificate is not valid but might become valid in future it is imported but not activated.
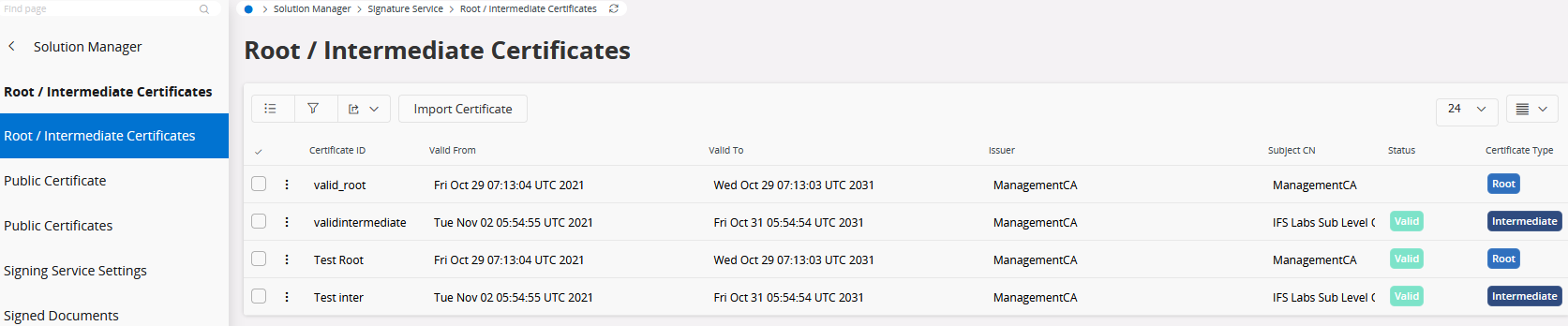
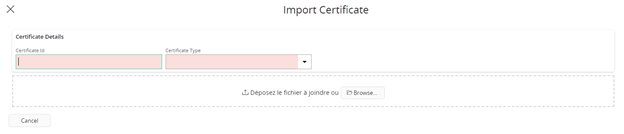
Importing certificates¶
Give the certificates a descriptive name and select the correct certificate type from the dropdown. The certificate must be in PEM format. Certificates will be saved only after validating those as valid certificates.
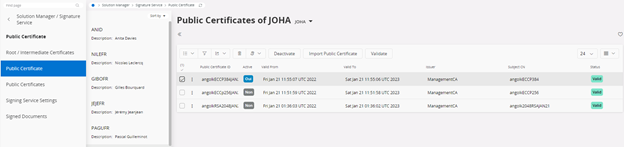
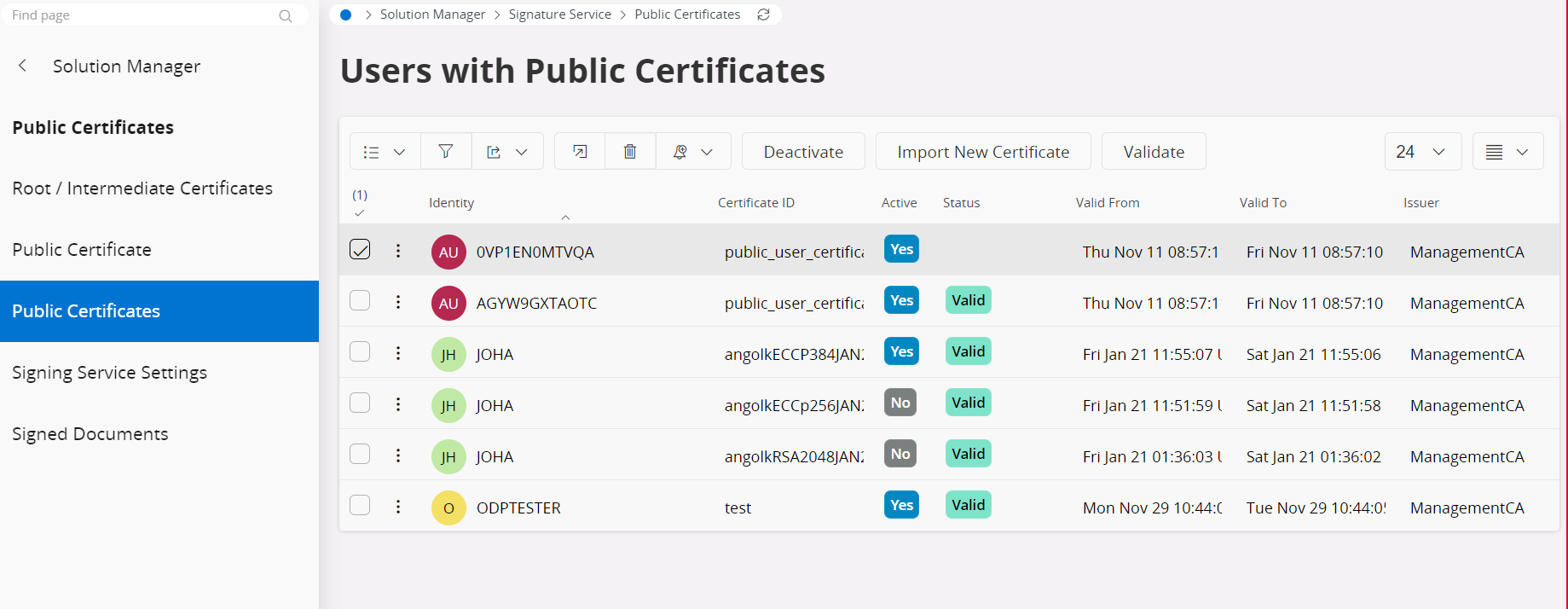
Register Public Certificates¶
Public certificates for an individual user can be imported from the solution manager. At a given time a user can have many public certificates attached to the user profile but only one valid and active certificate. When importing, if already active certificate is available, then an approval to deactivate the existing one needs to be given. User public certificates can be activated or deactivated according to the requirement.
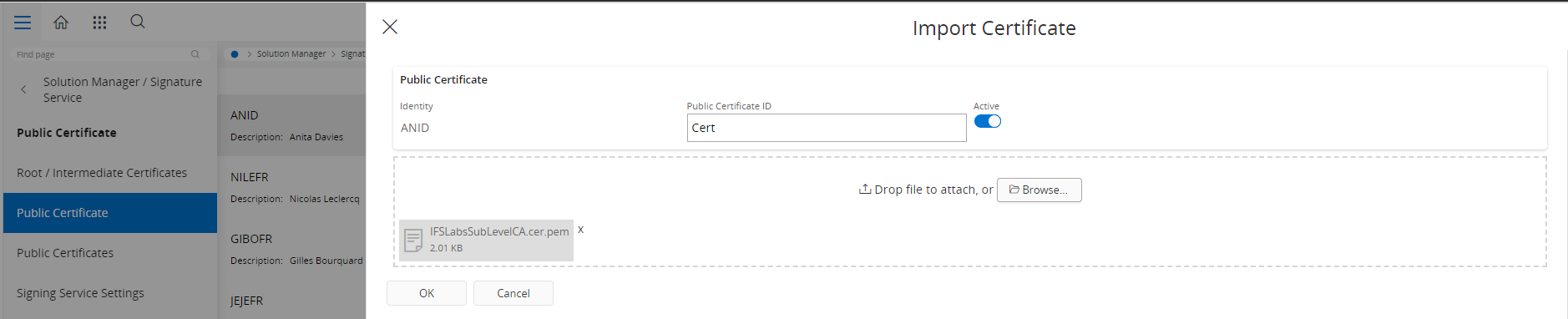
Importing certificates¶
Select the user and give the certificates a descriptive name. Set the active status for the certificate. The certificate file must be in PEM format. Certificates will be saved only after validating those as valid certificates.
All the public certificates of the users are listed in an overview page. A new public certificate can be imported to any selected user and the existing certificates can be validated on demand, deactivated and activated by using this overview page.
Timestamp Authorities¶
A Timestamp authority (TSA) gives a secure way of keeping track of the creation and modification time of a document. There is a default TSA configured out of the box but it likely required to use another source or even multiple sources. When more than one TSA is configured the first one defined will be used initially and if it fails it will continue to the next TSA in the list.
Digital Signature and Non Repudiation set¶
A certificate needs to have the non-repudiation and digital signing usages set to be properly qualified as a certificate intended to support document signing. Only certificates with these two usages set will be allowed to be imported as a user's public certificate by default. This behaviour, although not recommended, can be overridden in the settings by an administrator.
Permission Sets¶
Following permission sets has been introduced for signature service:
| Permission Set | Description |
|---|---|
| FND_DSS_ASST_ADMIN | Required grants of all the Digital Signature admin projections and Actions |
| FND_DSS_ASST_ENDUSER | Required grants of all the enduser related Projections and Actions for Digital Signature |
| FND_DSS_ASST_SERVICE | Required grants of Digital Signature service user |
Signature Extension¶
Extending documents are handled as a background job in the signature service. There are three separate jobs designed to handle extending from - Baseline-B to Baseline-T - Baseline-T to Baseline-LTA - Baseline-LTA to Baseline-LTA
The interval for each job can be scheduled using Solution Manager and uses quartz cron expression syntax.
The interval for Baseline-B to Baseline-T should be low to allow rapid extension for newly signed documents. In case a certificate gets invalidated the document must have been timestamped to show it was signed before it was invalidated otherwise it cannot be extended.
The interval for Baseline-T to Baseline-LTA does not need to be executed that often and is mainly depending on the CA used. If the certificate revocation list is updated once a day, it's enough to run this extension job to match that intervall.
The interval for Baseline-LTA to Baseline-LTA can be even longer since a document remains valid for a long time.
Each job is also picking up a certain number of documents to extend each time it runs which can be configured using the batch size setting. The batch size is meant to be used to achieve a balance if using multiple replicas. Simplified it means that the batch size can be large when using few replicas and lower if using many replicas to achieve evenly distributed load on each replica.
Storage¶
Signed documents can either be stored in the database or using File Storage Service(FSS).
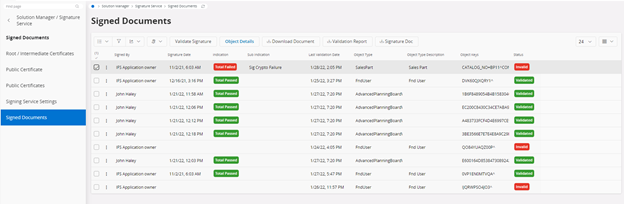
Signed Documents¶
The signed document page lists documents that were signed by the users. The authenticity of the signature can be verified with the validate signature option which is available on demand. The download options for the signed document, validation report, the signature as well as the link to the object details are available for the user for further details.
System Parameters¶
| Category | Parameter | Default Value | Description |
|---|---|---|---|
| Digital Signing Certs | Number of days ahead of expiration for notifications | 7 | The number of days before a certificate expires a notification should be sent. |
| Digital Signing Certs | Only allow public certificates with key usages: Digital Signature and Non Repudiation set | TRUE | Key usage check enforced. |
| Digital Signing Certs | Time Stamp Authorities | http://timestamp.digicert.com | Timestamp Authorities. There can be multiple TSA's defined. |
| Digital Signing Certs | Batch size for B to T Signature extending | 5 | Batch size used while extending from Baseline-B to Baseline-T. |
| Digital Signing Certs | Batch size for LTA to LTA Signature extending | 5 | Batch size used while extending from Baseline-T to Baseline-LTA. |
| Digital Signing Certs | Batch size for T to LTA Signature extending | 5 | Batch size used while extending from Baseline-LTA to Baseline-LTA. |
| Digital Signing Certs | Cron Job Schedule for B to T Signature extending | 0 */5 * ? * * | Interval used while extending from Baseline-B to Baseline-T. |
| Digital Signing Certs | Cron Job Schedule for LTA to LTA Signature extending | 0 0 12 ? * * * | Interval used while extending from Baseline-T to Baseline-LTA. |
| Digital Signing Certs | Cron Job Schedule for T to LTA Signature extending | 0 */30 * ? * * | Interval used while extending from Baseline-LTA to Baseline-LTA. |
| Digital Signing Certs | Storage option to store Digitally Signed Documents | DB/FSS | Storage for digitally signed documents. |