Secured Communication¶
Overview¶
IFS Cloud requires secured communication (HTTPS) for all installation types. This implies that all clients that connects to the IFS Cloud Middle Tier have to have or obtain trust to the certificate used by the web server / proxy. The certificate to trust might be issued to either the webserver inside kubernetes itself or an external proxy.
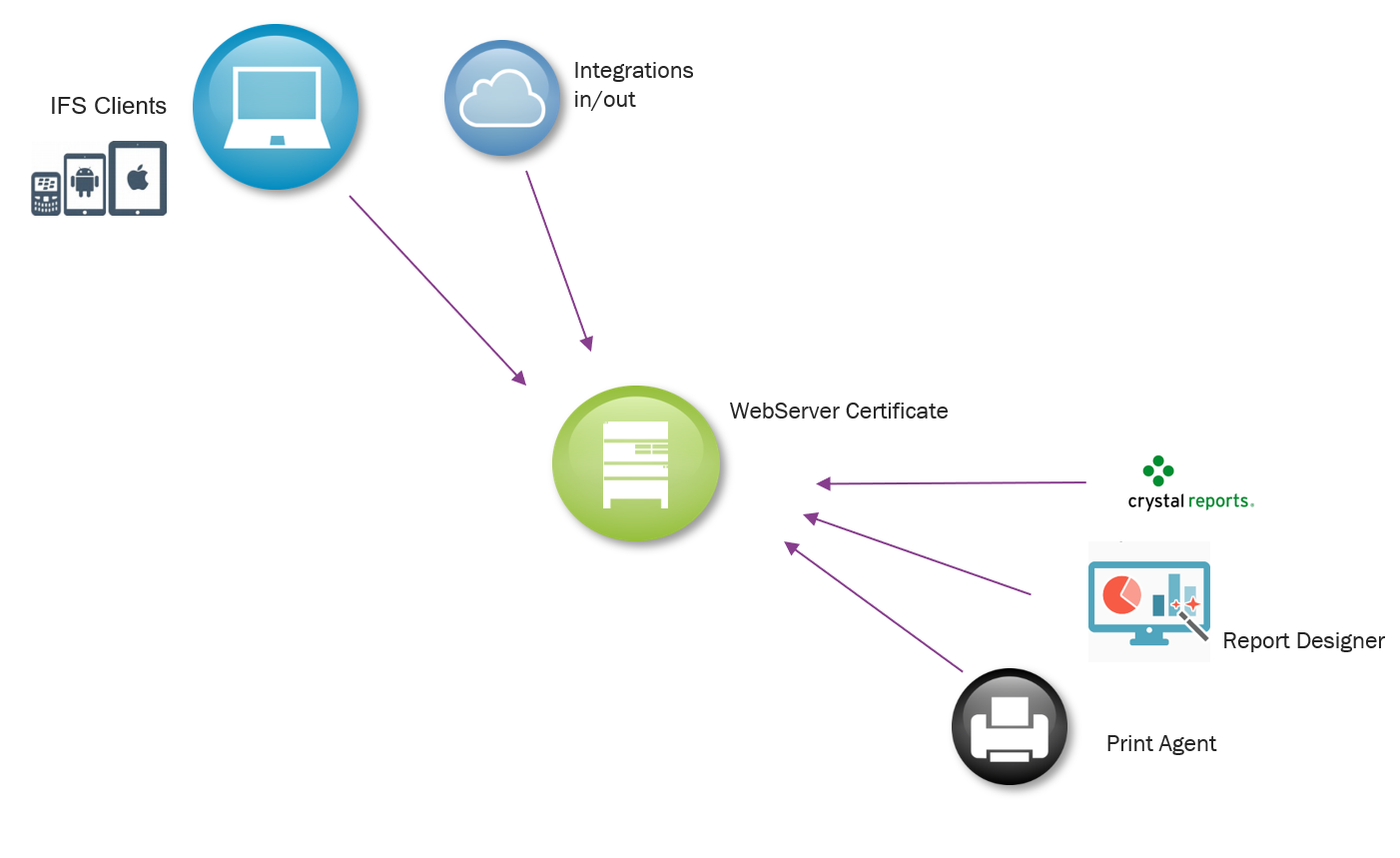
Client Certificates¶
When connecting to any server that require secure communication the client must trust the keys that the server offers to encrypt the traffic. The client must trust that the key is actually coming from the server the client thinks its connection to. Together with the encryption keys (Public keys) the server sends a signed Certificate that refers to the CA that signed the Servers Certificate. IF the client trust that specific CA then the client will also trust that the keys comes from a trustworthy server and use the keys. The client knows when to trust a specific CA if the CA is in the clients truststore.
On a windows client this list of trusted CA's can be seen using the application "certmgr" from a cmd prompt.
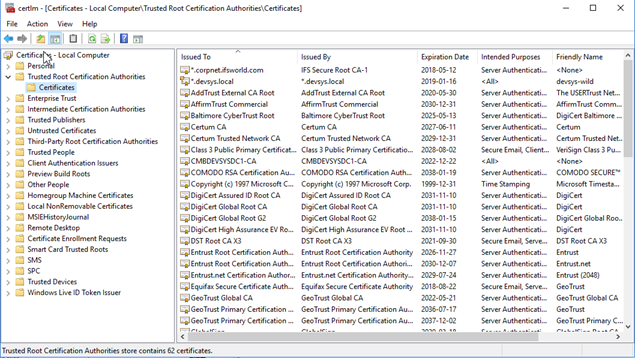
Right-Mouse-Click on "Certificates" will allow new certificates to be imported in certmgr.
Manually fetching and approving a client certificate (CA trust)¶
Normally it is possible to use the Internet browser for to fetch a client certificate and manually approve the validity of the certificate. This is done by pointing out the web url and accepting the certificate in the browser. Most of browsers offer possibility for exporting the downloaded certificates.
If you need to import certificates from third party web services they need to be fetched first. It is possible to use the Internet browser for this purpose by pointing out the third-party web service and accepting the certificate in the browser. Most of browsers offer possibility for exporting the downloaded certificates.
But it is also possible to use command line tools for fetching the certificate: openssl and sed. Both those tools are typically preinstalled on Linux but must be downloaded and installed on Windows.
The command looks as follows:
Linux:
openssl s_client -connect <hostname>:<port> < /dev/null | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' > <certificate.crt>
Windows:
openssl s_client -connect <hostname>:<port> < NUL | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' > <certificate.crt>
Use Client Certificate in IFS Middle Tier¶
Certificates can be imported in the installation process in Remote deployment models by specifying location in the configuration ifscloud-values.yaml file or add the certificate as clear text in the ifscloud-values.yaml. To add a client certificate to a specific pod see the section "Specific Certificate for pods" in Installation parameters
To add client certificates for normal connect integrations use Solution Manager in the the IFS Client. There you can upload certificates on e.g. the routing addresses or sftp's.