Authorization Code flow¶
Authorization Code Flow is the ideal way to authenticate against IFS Cloud to get an access token. During this flow, the client application will use a browser (either the system browser or an embedded browser control) to render the login page and perform authentication.
Step 1: The client application sends a request to the authorization endpoint in the authorization server(IFS IAM)
GET<AUTHORIZATION_ENDPOINT>?client_id=<IAM_CLIENT_ID>&response_type=code&scope=openid microprofile-jwt&redirect_uri=<REDIRECT_URI>&state=<GUID>&nonce=<RANDOM_STRING>
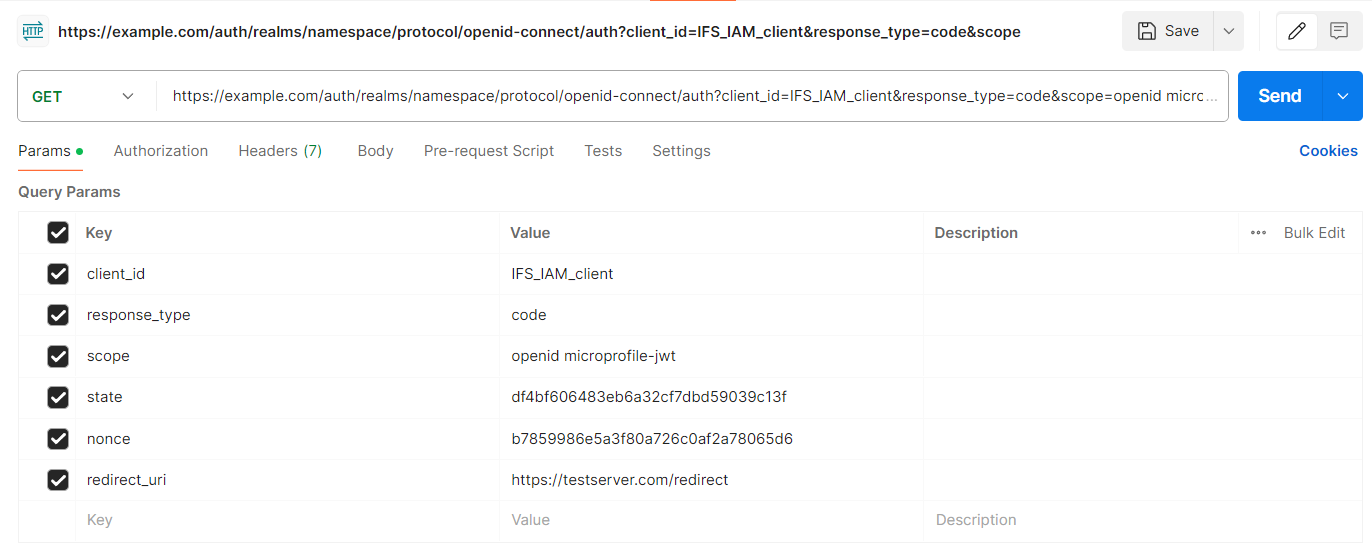 Sample Authorization endpoint request
Sample Authorization endpoint request
client_id: The Client ID of the IFS IAM client
response_type: Denotes the use of the Authorization Code Flow. Should use the value “code“
scope: Should be set to “openid microprofile-jwt“
state: A random GUID used for client application in order to correlate different steps within the same flow
nonce: Cryptographic nonce used to mitigate replay attacks. A randomly generated string that has sufficient entropy to prevent attackers from guessing values.
redirect_uri: The redirect URI configured in the client. Refer Setting up redirect URI section for more info.
NOTE: The Authorization endpoint can be found in the Open ID Discovery endpoint.
https://<SYSTEM_URL>/auth/realms/<NAMESPACE>/.well-known/openid-configuration
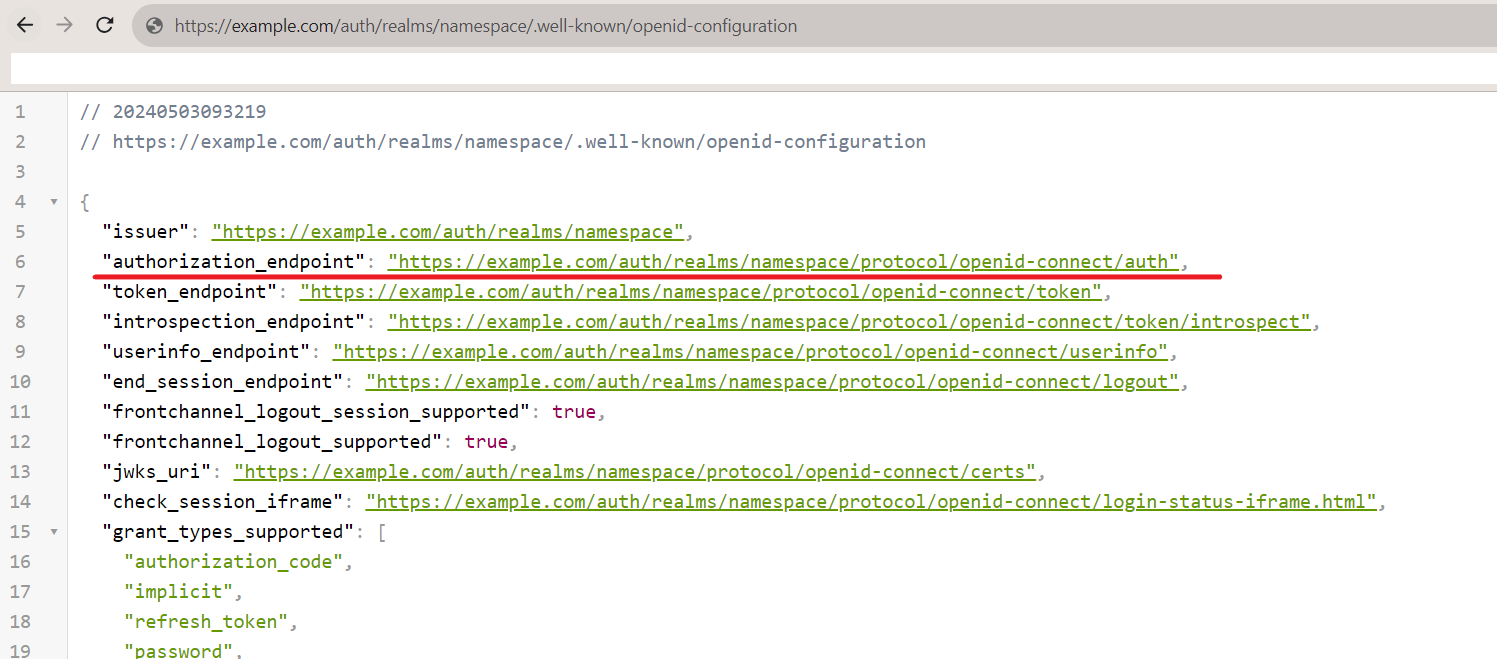 Sample open id configuration
Sample open id configuration
Step 2: The browser will render the login page of the application and perform authentication in whichever manner has been configured. Here, the login experience will be the same as the one that is recognized for IFS Cloud Web or IFS Cloud Mobile. All the same features of authentication are available at this point, such as SSO and the use of external Identity Providers.

Rendered login page
Step 3: Upon entering valid credentials on the login page, IFS IAM will authenticate the user and redirect the browser to the specified redirect URI with some new query parameters.
Step 4: The client application will extract the code query parameter from the URL which the IAM redirected to and send a request to the token endpoint
POST https://<SYSTEM_URL>/auth/realms/<NAMESPACE>/protocol/openid-connect/token
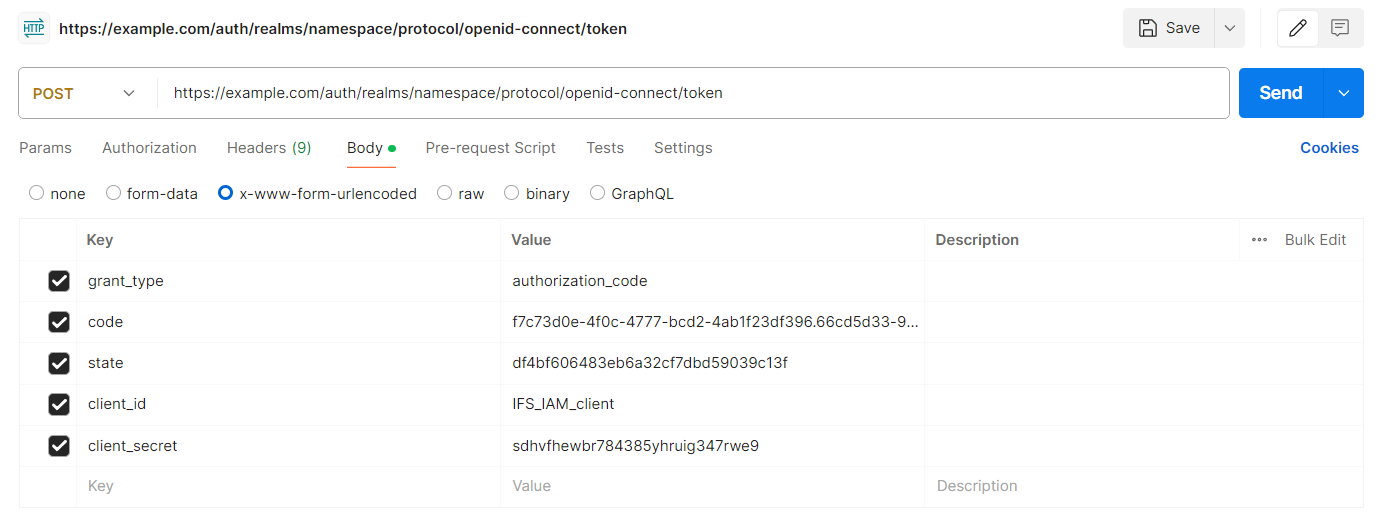 Sample token endpoint request in authorization code flow
Sample token endpoint request in authorization code flow
grant_type: Denotes the use of the Authorization Code Flow. Should use the value “authorization_code“
code: The one-use code extracted from the URL which the IAM redirected to
state: The same random value which was used for the first request to the Authorization Endpoint.
client_id: The Client ID of the IFS IAM client
client_secret: The Client secret of the IFS IAM client
The client application will get a response in the following format for the above token endpoint request:
{
"access_token": "<NEW_ACCESS_TOKEN>",
"expires_in": 180,
"refresh_expires_in": 1800,
"refresh_token": "<NEW_REFRESH_TOKEN>",
"token_type": "Bearer",
"id_token": "<NEW_ID_TOKEN>",
"not-before-policy": 0,
"session_state": "<SESSION_STATE>",
"scope": "openid audience microprofile-jwt email profile"
}
The access_token element is extracted and used as the bearer token to access the IFS Cloud backend APIs and the refresh_token can be used to refresh access tokens as they expire.
The below illustration shows a high-level view of the flow mentioned above:
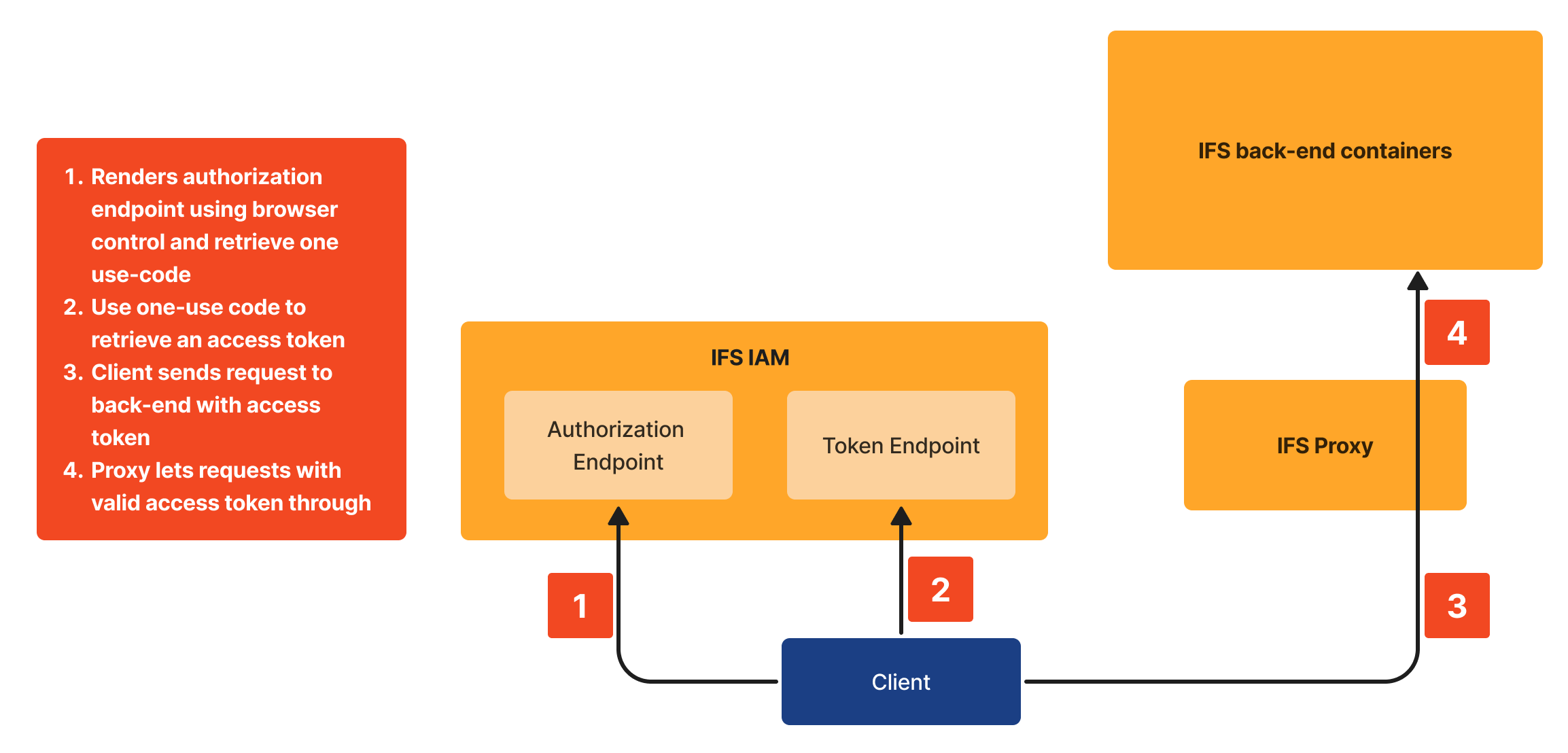 Bearer token usage with Authorization Code Flow
Bearer token usage with Authorization Code Flow