Client Credential Flow¶
For applications that are incapable of rendering a browser and do not need end user accounts in order to access the system to do some limited tasks, the Client Credentials flow allows for a non-interactive authentication of a service account where the authorization endpoint is never contacted and the request is done non-interactively directly to the token endpoint using pre-configured credentials. This form of authentication yields an access token associated with a service user that is associated with the IAM client itself rather than an end user account. The client ID and client secret of a client registration set up to allow this flow act as the username and password for the integrating application.
POST https://<SYSTEM_URL>/auth/realms/<NAMESPACE>/protocol/openid-connect/token
grant_type: Denotes the use of the Client Credential Flow. Should use the value “client_credentials“
scope: Should be set to “openid microprofile-jwt“
client_id: The Client ID of the IFS IAM client
client_secret: The Client secret of the IFS IAM client
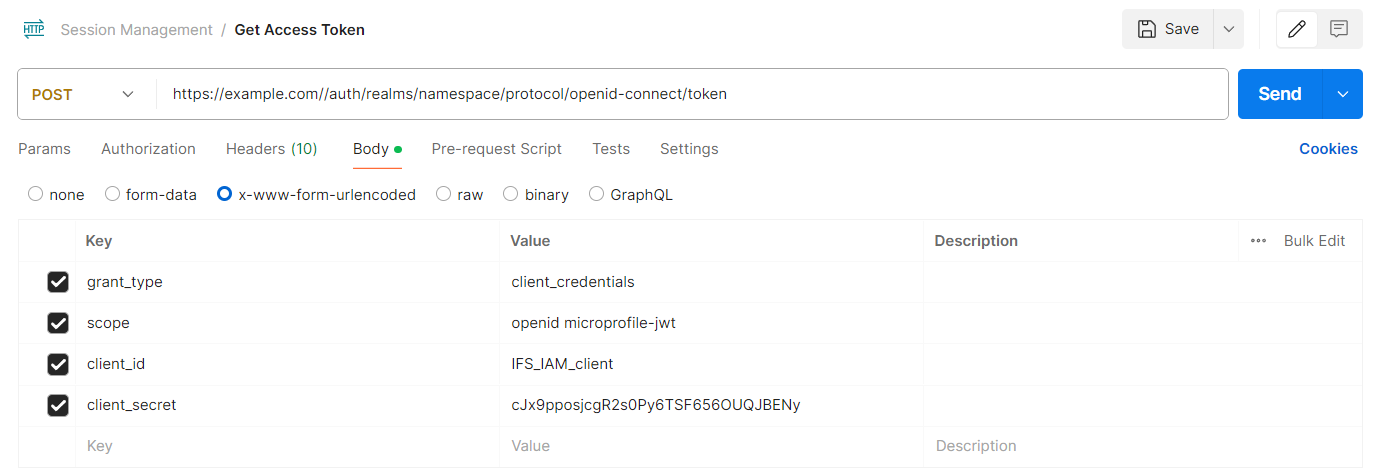 Sample token endpoint request in client credential flow
Sample token endpoint request in client credential flow
The client application will get a response in the following format for the above token endpoint request:
{
"access_token": "<NEW_ACCESS_TOKEN>",
"expires_in": 180,
"refresh_expires_in": 1800,
"refresh_token": "<NEW_REFRESH_TOKEN>",
"token_type": "Bearer",
"id_token": "<NEW_ID_TOKEN>",
"not-before-policy": 0,
"session_state": "<SESSION_STATE>",
"scope": "openid audience microprofile-jwt email profile"
}
The access_token element is extracted and used as the bearer token to access the IFS Cloud backend APIs and the refresh_token can be used to refresh access tokens as they expire.