Authorization Code Flow with PKCE¶
Since the use of a public client means that the IAM client does not use client secrets to secure the token endpoint, it is highly recommended to use a standard called Proof Key For Code Exchange or PKCE. For this, the authorization endpoint request will include another two query parameters called code_challenge and code_challenge_method while the token endpoint request will include another query parameter called code_verifier.
GET <AUTHORIZATION_ENDPOINT>?client_id=<IAM_CLIENT_ID>&response_type=code&scope=openid microprofile-jwt&state=<GUID>&nonce=<RANDOM_STRING>&redirect_uri=<REDIRECT_URI>&&code_challenge=<CODE_CHALLENGE>&code_challenge_method=<CODE_CHALLENGE_METHOD>
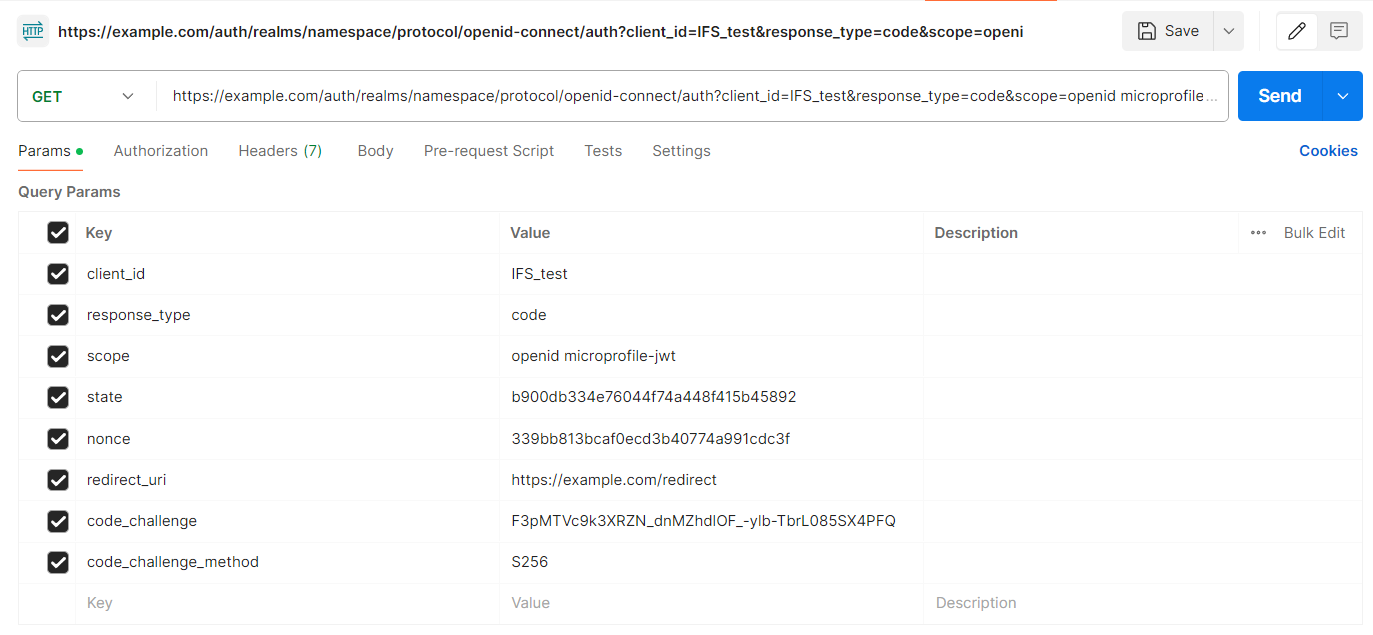 Sample Authorization endpoint request with PKCE
Sample Authorization endpoint request with PKCE
code_verifier: A random string with at least 43 characters and at most 128 characters
code_challenge: If the code_challenge_method is S256, then the code_challenge should be calculated
code_challenge = BASE64URL-ENCODE(SHA256(ASCII(code_verifier)))
If the code_challenge_method is plain, then the code_challenge should be the same as the code_verifier.
code_challenge_method: Can be either S256 or plain
POST https://<SYSTEM_URL>/auth/realms/<NAMESPACE>/protocol/openid-connect/token
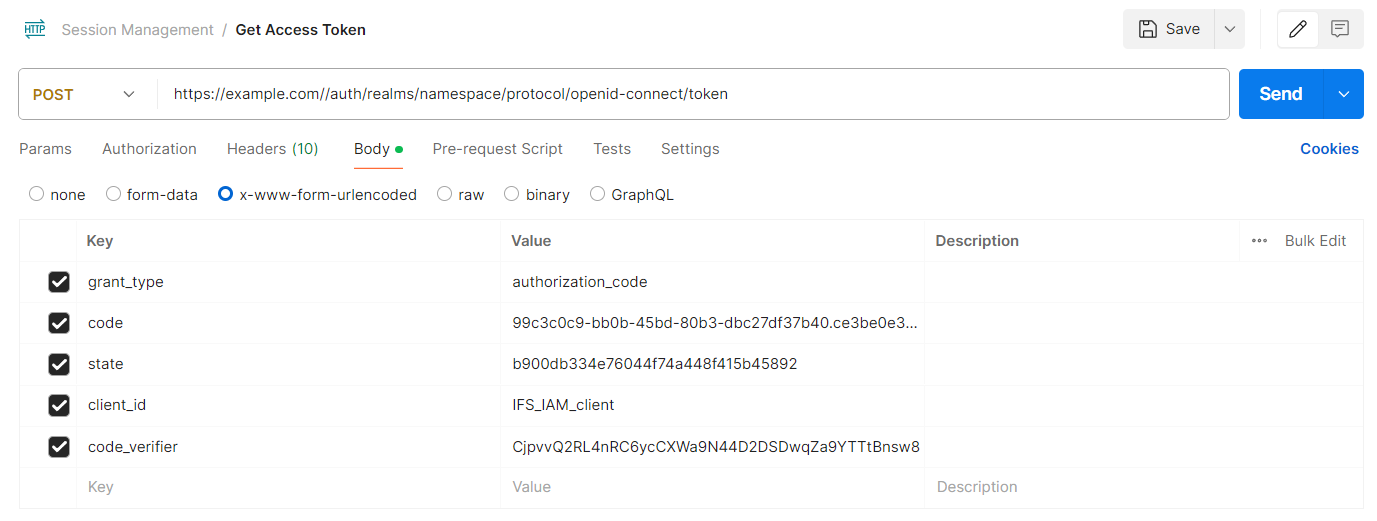 Sample token endpoint request in authorization code flow with PKCE
Sample token endpoint request in authorization code flow with PKCE