Using Access Token to access IFS Cloud endpoints¶
If the client application uses the Authorization Code flow, Client Credentials Flow or Resource Owner Password Credentials Flow the access token retrieved from the IAM can be used as a Bearer token in the HTTP requests. This can be done by attaching the access token in the Authorization HTTP header.
Authorization: Should be set to “Bearer
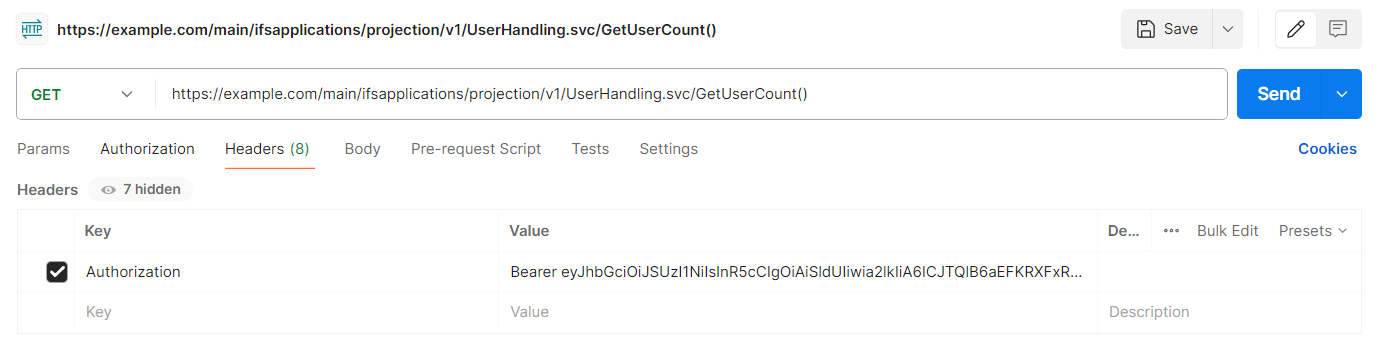 Sample IFS cloud API request that uses Bearer token to authenticate
Sample IFS cloud API request that uses Bearer token to authenticate
Refreshing Token¶
Since the access token is short-lived (to be set to 3 minutes in 24R2), the client application will have to authenticate and get a new access token frequently to access the system. Therefore the best approach to avoid frequent authentication is to implement a refresh token mechanism in the client application.
If the access token is invalid the client application will get a 401 unauthorized error as follows when accessing IFS cloud backend APIs.
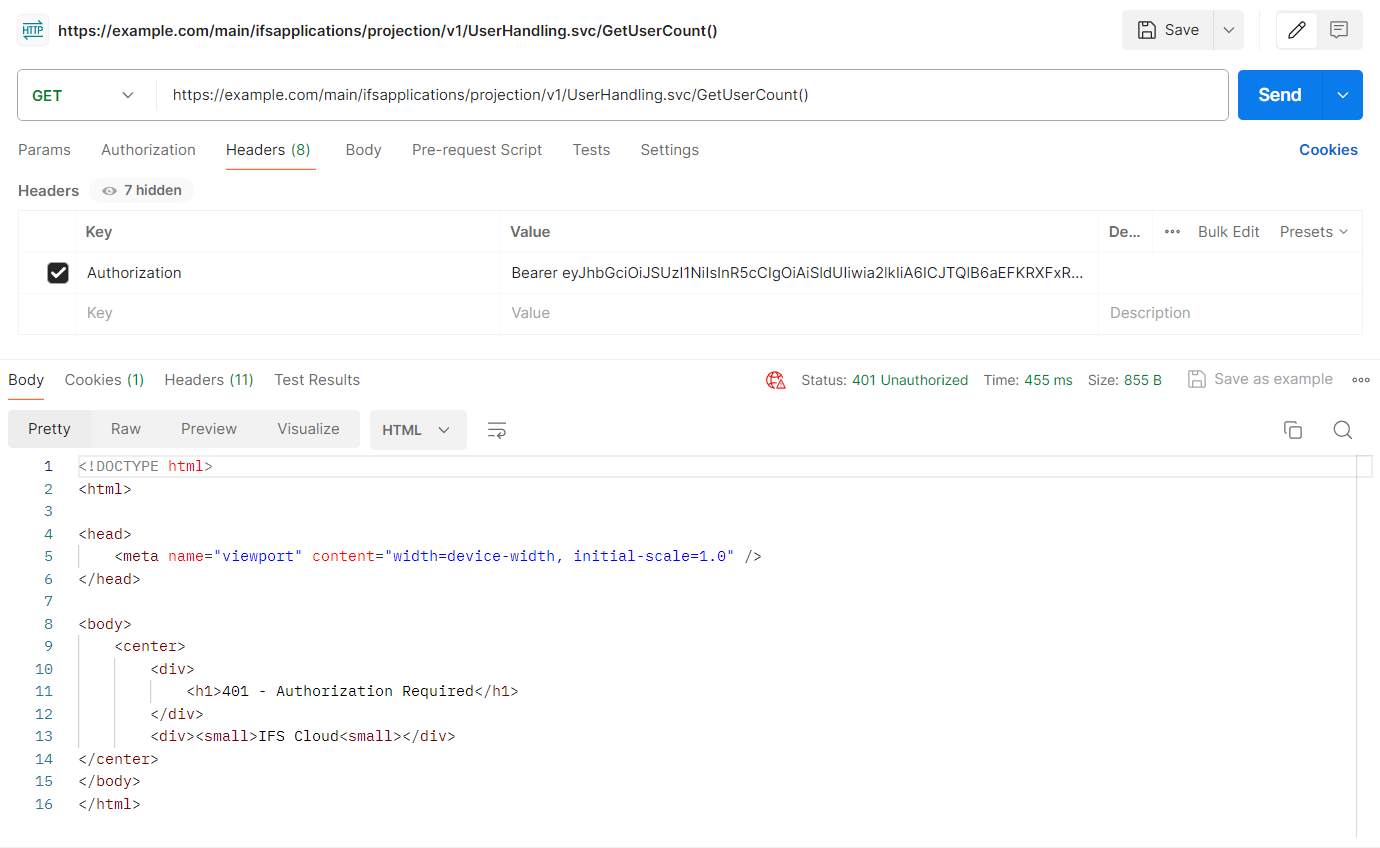 401 unauthorized error when access token expired
401 unauthorized error when access token expired
Implementing a refresh token mechanism¶
As mentioned in the above flow, every time a new access token is retrieved the client application will get a refresh token as well. This refresh token can be used to get another new access token when the current access token expires. For that same token endpoint can be used.
POST https://<SYSTEM_URL>/auth/realms/<NAMESPACE>/protocol/openid-connect/token
refresh_token: Refresh token extracted from the last token endpoint response
grant_type: Denote the use of token refresh flow. Should use the value “refresh_token“
client_id: The Client ID of the IFS IAM client
client_secret: The Client secret of the IFS IAM client
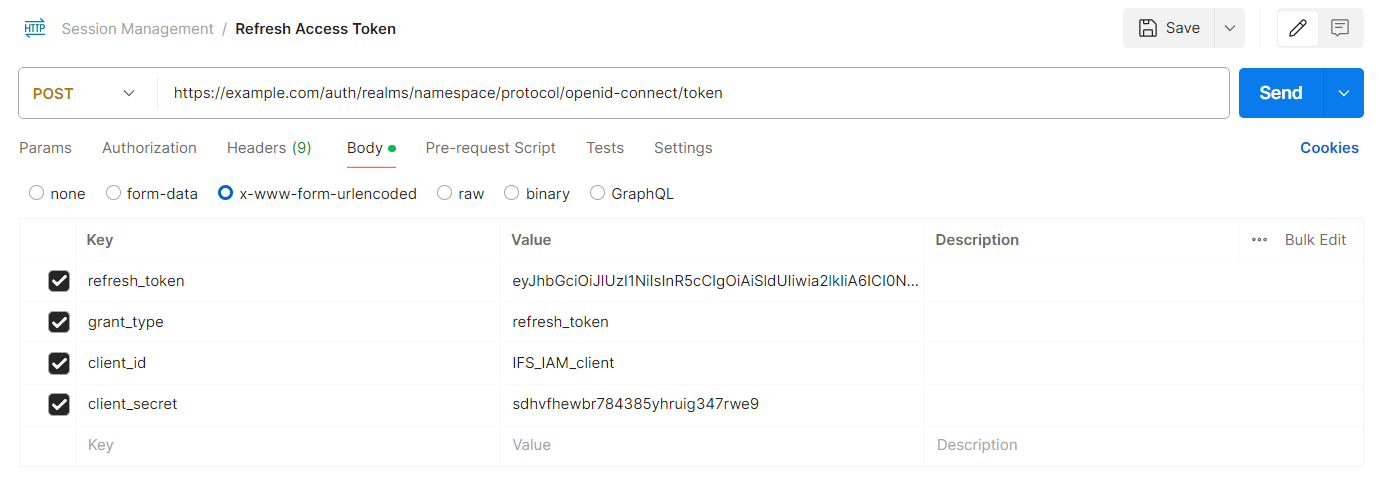 Sample refresh token endpoint request
Sample refresh token endpoint request
The client application will get a response in the following format for the above token endpoint request:
{
"access_token": "<NEW_ACCESS_TOKEN>",
"expires_in": 180,
"refresh_expires_in": 1800,
"refresh_token": "<NEW_REFRESH_TOKEN>",
"token_type": "Bearer",
"id_token": "<NEW_ID_TOKEN>",
"not-before-policy": 0,
"session_state": "<SESSION_STATE>",
"scope": "openid audience microprofile-jwt email profile"
}
The access_token element is extracted and used as the bearer token to access the IFS Cloud backend APIs and the refresh_token can be used to refresh access tokens as they expire.
NOTE: Every time the client application requests a new access token, it will receive a new refresh token along with that. This new refresh token should be used to get the next new access token and the old refresh token should be disposed of.
Once you have implemented your authentication integration;
- Test your integration thoroughly to verify and ensure proper authentication functionality. Regular monitoring is also recommended.
- Ensure that any sensitive credentials are securely stored and transmitted. Use encryption and other security best practices to protect against unauthorized access.
By following these steps, you can securely authenticate your external integration for smooth communication between your system and the external service.