Configuring Authentication for Integrations¶
This document describes how to set up external systems to be able to authenticate towards IFS Cloud. The IFS IAM accomodates many different flows in order to be able to service different clients with different authentication needs. In order for a client to authenticate to IFS Application it needs to retrieve an access token from the IAM. There are several ways to do this and the sections below describe what configurations have to be done in order to enable these different ways depending on the clients used. All different flows are described on a conceptual level here.
General process and terms¶
The process of setting up an integration using OAuth2 has the fundamentally same characteristics in all cases and is described in several different ways in the OAuth2 specification. This documentation will attempt to use the terms as they are presented in the specification. The integrating system is called an OAuth2 client (the OAuth2 specification uses the term "client" but we chose to use a more specific term since the OAuth2 concept of a client is different from how the term is commonly used). The OAuth2 client is supposed to contact a service called an authorization server in order to retireve an access token and then use this to access protected resources on the resource server. In the case of IFS, the role of the authorization server is played by the IFS IAM and the protected API:s of the IFS Cloud containers play the role of the resource server. The general structure of the process is illustrated below.
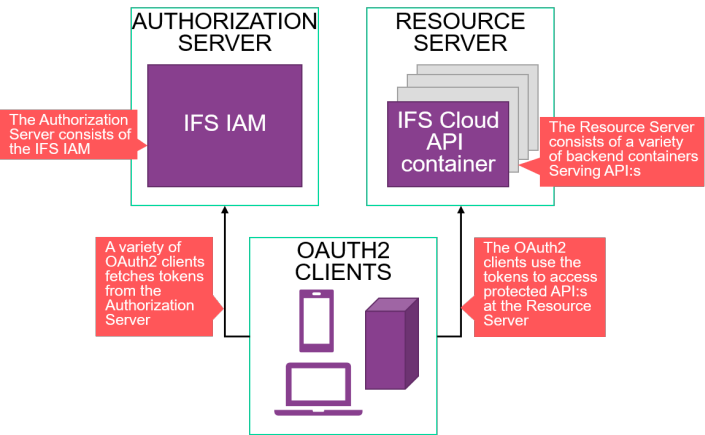
There can be a variety of OAuth2 clients running on different architectures. They can be serverside processes, a third party web application with serverside logic, a single page browser application or a natively installed application on a computer or mobile device. What unites them is that they are clients in the OAuth2 sense as illustrated above, in which they use access tokens that they get from making calls to the authorization server and use them to access resources on the resource server. This relationship is consistent throughout all flows and all kinds of applications. The main difference between different integrations towards IFS Cloud is how they go about getting the token from the IFS IAM. This differs depending on the nature and specific needs of the integration.
Supported Flows¶
The supported flows for authenticating can be referenced here: