Third-Party Apps Integration with CSRF Prevention Mechanism Enabled¶
This is only applicable to third-party applications which are integrated with main | b2b endpoints. Since our intention here is only to show how the CSRF tokens are set, we will use “int” endpoint with BASIC authentication. This simulates the scenario for main, b2b endpoints whenever JSESSIONID is used as well.
Using Logic Apps with CSRF prevention mechanism enabled¶
Logic apps can be configured to work with CSRF protected projections by sending the XSRF-TOKEN cookie and X-XSRF-TOKEN header value with each protected resource call, using direct http calls.
Following is an example Logic app which use aforementioned CSRF mitigation mechanism.
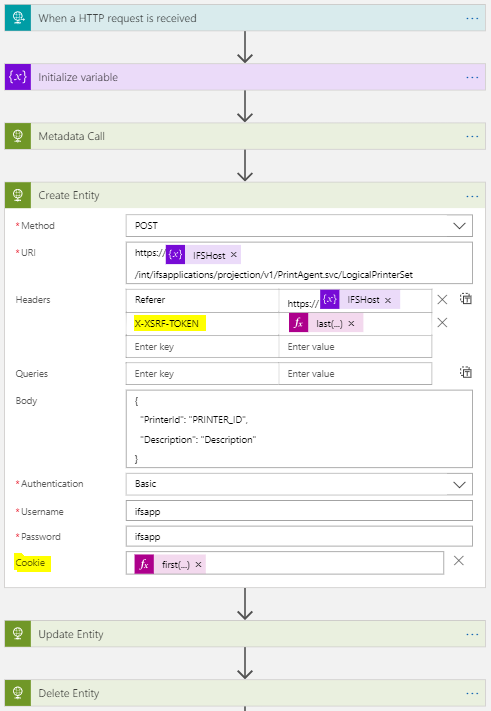
In the above Logic app first we make a GET request to retrieve metadata. ( which also returns the CSRF cookie ). Then this cookie and extracted X-XSRF-TOKEN header value is sent with all subsequent requests which manipulate protected resources.
Using Power Apps with CSRF prevention mechanism enabled¶
Power apps can be configured to work with CSRF enabled projections by sending the XSRF-TOKEN cookie and X-XSRF-TOKEN header value with each protected resource call. Here we have to rely on a Azure based tool called Flows. Again this only works with direct http calls.
Following is an example Power app which use aforementioned CSRF mitigation mechanism.
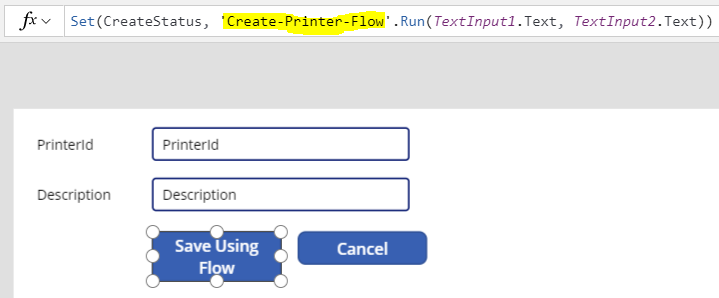
Following is the Flow used to create the entity.
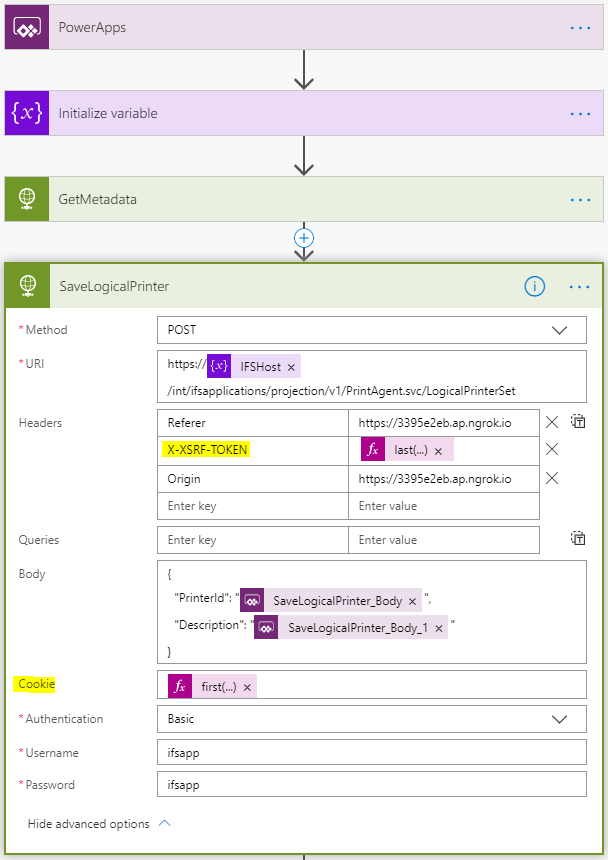
In the above Power app Flow first we make a GET request to retrieve metadata. ( which also returns the CSRF cookie ). Then this cookie and extracted X-XSRF-TOKEN header value is sent with the create request.
For more details about CSRF implementation, follow this link.